THE CHALLENGE:
In the rapidly evolving field of wireless communications, the advent of 5G and the forthcoming 6G technologies have significantly increased the demand for high-speed, reliable connectivity. As wireless networks are deployed in diverse and complex environments such as conference rooms, secure facilities, and urban areas, there is a crucial need for precise management of signal distribution. Effective geofencing mechanisms are essential to dynamically define and control wireless service areas, ensuring optimal performance, enhancing security, and minimizing interference in densely populated or sensitive locations.
However, current approaches to managing wireless signal propagation often fall short in addressing dynamic and heterogeneous modern networks. Traditional methods typically rely on static infrastructure or control over transmitters to direct or block signal beams. These techniques lack the flexibility to rapidly adapt to changing environmental conditions. They may also be unfeasible to achieve in many real-world network scenarios, where, for instance, indoor hosts cannot control outdoor transmitters operated by a third-party mobile operator, preventing the indoor host from temporarily isolating specific network areas and resulting in unwanted wireless network service coverage.
OUR SOLUTION:
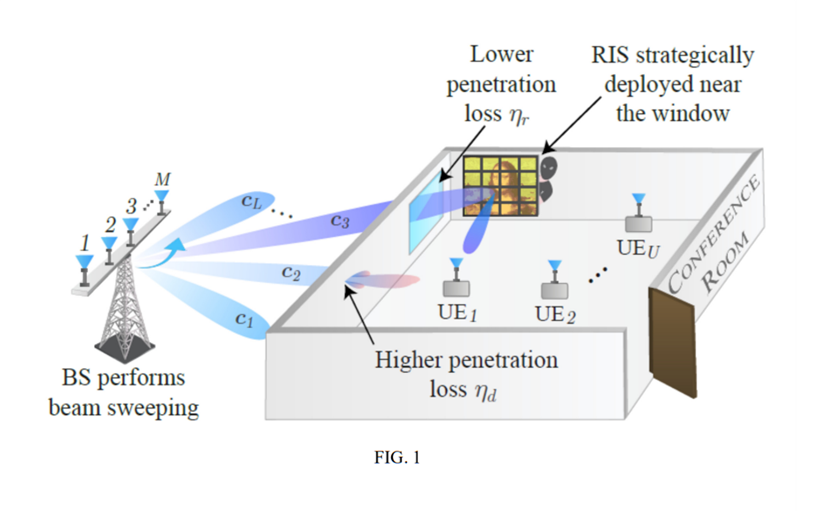
This system utilizes reconfigurable intelligent surfaces (RIS) to dynamically manage wireless signal propagation, effectively establishing geofenced areas for wireless services, including communications and sensing. By adjusting electromagnetic properties such as reflection, refraction, and absorption, the RIS manipulates beam determination during the initial access phase of wireless communication to induce beam misalignment during the data transmission phase, hindering communication in certain network service areas. During beam sweeping, the system alternates between reflecting and absorbing signals to direct transmitter-receiver connections through the RIS. In the data transmission phase, the RIS switches to absorption mode to block signal propagation within the defined area. An advanced implementation incorporates a combinatorial multi-armed bandit (CMAB) algorithm based on reinforcement learning, which optimizes the RIS’s reflection and absorption patterns without needing channel state information. This allows for efficient learning and application of optimal configurations, providing precise and flexible control over wireless coverage in environments like conference rooms or secure facilities.
The technology is differentiated by its innovative use of RIS for creating dynamic virtual geographic boundaries in 5G and 6G systems without channel state information. A proposed CMAB approach leverages reinforcement learning to make informed decisions on RIS configurations, significantly reducing average user spectral efficiency and increasing spatial outages in simulations. This method excels in scenarios with high direct path penetration loss and low reflected path loss, as those illustrated in Fig. 1. Additionally, the system provides advantages such as operation without channel state information, dynamic and reversible control of coverage areas, quick service restoration, and flexible implementation through software algorithms. These unique features make it highly attractive to RIS manufacturers, telecommunications vendors, network operators, and cybersecurity companies.
ADVANTAGES:
- Operates without the need for channel state information
- Provides dynamic and precise control of wireless coverage
- Enables reversible geofencing, restoring normal service upon deactivation
- Allows quick service restoration
- Flexible implementation through software-based algorithms
- Enhances wireless security in environments like conference rooms and secure facilities
- Facilitates controlled shielding of specific network service areas
- Capable of autonomous operation
POTENTIAL APPLICATIONS:
- Conference room communication control
- Secure facilities management
- Examination environment control
- Classified meeting security
- Wireless security applications